Security researchers recently detected a curious case of entrapped PDF file hosted in Azure Blob storage. More specifically, the case involves storing the attackers’ phishing form on Azure Blob Storage in order to be secured by a Microsoft SSL certificate.
The entrapped PDF is linked to an Office 365 phishing page hosted in Azure Blob storage, and because of that, it has a Microsoft-issued domain and SSL certificate, Netskope researchers discovered.
It should be noted that the combination of the Microsoft domain, certificate, and content make this phishing scheme particularly convincing and difficult to recognize. During their analysis, the researchers identified similar phishing sites hosted in Azure blob storage.
The Azure Blob Phishing Attack Explained
As in any phishing scenario, the malicious PDF are delivered to victims as email attachments. These are crafted in a smart way, containing legitimate content from legitimate sources.
“In this case, the document originally arrived in an email and was saved to Google Drive, where Netskope Advanced Threat Protection detected the file and prevented potential credential loss or fan-out“, the researchers noted.
Analysis of the PDF
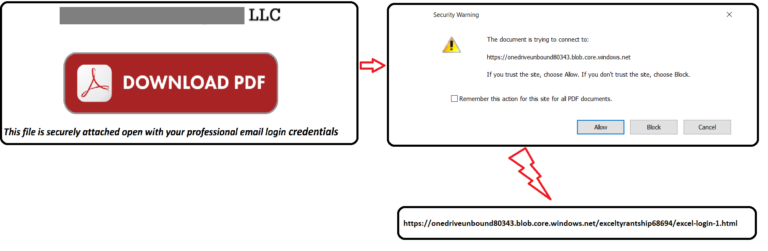
The PDF distributed in this particular phishing campaign impersonates a law practice based out of Denver. It was named “Scanned Document… Please Review.pdf”. The PDF has a link that downloads the actual PDF:
Once the “Download PDF” hyperlink is clicked, the victim sees a message explaining that the document is trying to connect to the following Azure blob storage URL – https://onedriveunbound80343[.]blob.core.windows.net:
The phishing page is hosted in Azure blob storage which assures a valid Microsoft-issued SSL certificate and hosting on a Microsoft-owned domain. These two factors make the phishing attempt quite sophisticated and difficult to recognize. As pointed out by the researchers, “seeing a Microsoft domain and a Microsoft-issued SSL certificate, on a site asking for Office 365 credentials is pretty strong evidence that the site is legitimate, and are likely enough to convince a user to enter their credentials”.
Once the user clicks, his credentials are uploaded to this location: https://searchurl[.]bid/livelogins2017/finish40.php. Then, the user is redirected to another phishing page hosted in blob storage.
Later on, the user is going through a series redirects to several landing pages posing to download the secured document. Finally, the user is finally redirected to a Microsoft page, but no document is downloaded to the victim’s machine. As the document is not downloaded, the victim might again try to re-validate the credentials or enter credentials related to another account.
To counter such phishing attackers, the researchers’ recommendation is always checking the domain of the link, and:
Know the domains typically used when you login to sensitive services. Additionally, be able to identify common object store domains, such as those used by Azure blob storage. This knowledge will help you differentiate between well-crafted phishing sites and official sites.