A security team has detected ongoing LinkedIn phishing attacks that aims to infect users worldwide. Further information about the threat is given in this article.
LinkedIn Phishing Attacks Unleashed By Unknown Hackers
A security research team has discovered a series of ongoing LinkedIn phishing attacks. According to the released report the criminals use various strategies in order to coerce the victims into visiting malware pages. The essence of these types of infections is produce notifications, messages and pages that present a convincing copy of the legitimate web service or other related sites.
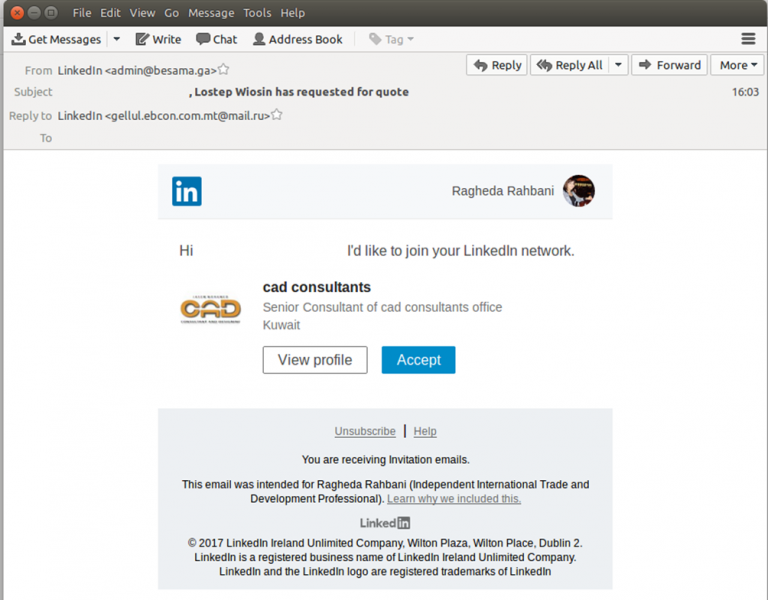
Instead of sending in-service messages the criminals have taken the legitimate text and graphics used by LinkedIn and designed identical looking emails. Once this was done they embedded malware hyperlinks into the false notifications that resemble actual LinkedIn connection requests. The customized instances were then sent to the victims using various domains. One of the main ones is admin@besama.ga which is currently inactive. Security experts and experienced system administrators can uncover certain inconsistencies that can easily expose the scam:
- Fake Email Address — The hackers use a fake address both as the incoming sender, as well as the one listd in the “reply” field.
- Option Redirect — Once the users click on a link they will be redirected to a malware login page that is designed to look like LinkedIn.
At the moment there is no information on how the criminals behind it have obtained the target emails. It is possible that this is done via data harvested from browser hijackers and malware sites. They are created in bulk and form large networks that are under hacker control. Even if the contact emails do not belong to people that have been infected themselves prior to the LinkedIn phishing attacks, it is suspected that people related to them have given been infected. One of the interesting highlights of this campaign is the fact that the criminals use a trick that attempts to cover their tracks. This is done using timed malware links that can expire once interacted. The experts use various legitimate sites in signatures and other related materials in the messages. This hybrid approach used can also evade certain spam filters and security precautions.
Consequences of the LinkedIn Phishing Attacks
Once the victims interact with the hyperlink they will be shown a counterfeit LinkedIn login page. If the users enter their credentials they will be immediately given to the hacker controllers.
However this is not the only malware scenario that can happen. Such behavior can also be linked to the following cases:
- Malware Delivery — The pages can link to malware of different types, including viruses, ransomware, Trojans and etc.
- Browser Hijacker Installation — In some cases the hackers may utilize scam tactics to deliver fake LinkedIn extensions and other types of browser hijackers. They are advertised as useful additions or as an official component made by LinkedIn’s team. Once installed they alter default settings (home page, new tabs page and search engine) to hacker-controlled ones. Another effect upon the victims is the installation of a tracking module that collects both anonymous and private user data.
- Malware Scripts — The criminals can embed various scripts that can lead to the creation of pop-ups, banners and other distracting content. They are forms of target advertisement in most cases.

LinkedIn Phishing Email Scam Detected
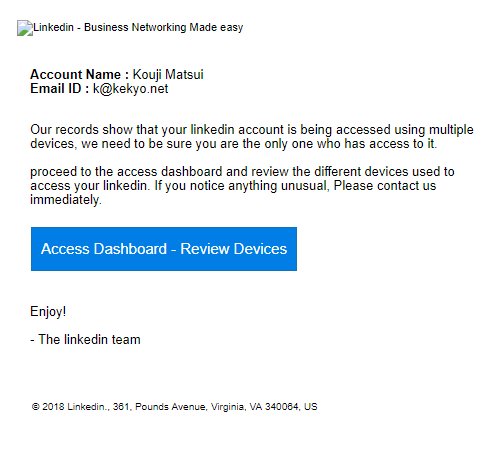
We have received reports about a new LinkedIn phishing scam scheme which takes advantage of a social engineering tactic. The hacker operators will send out personalized email messages containing the user’s Account name and email address. The quoted information is extracted by the infection engine by automatically visiting the user’s profiles and hijacking the requested data. This is then fed to the email generation module which is responsible for the creation of the messages.
If the users interact with the site they will be redirected to a fake login page asking for their account data. If it is entered then the hacker operators will automatically receive them and use them for identity theft and other crimes. Other possible consequences include blackmail of the victims and the upload of the account data to databases which may be sold for profit to interested buyers: marketing agencies or other hackers.
The use of a quality anti-spyware solution can help protect the victims from possible malware infections.
Spy Hunter scanner will only detect the threat. If you want the threat to be automatically removed, you need to purchase the full version of the anti-malware tool.Find Out More About SpyHunter Anti-Malware Tool / How to Uninstall SpyHunter