Security researchers have just discovered several vulnerabilities in some SSDs that could allow a threat actor to bypass the disk encryption feature and access local data. To do that, the attacker doesn’t need to know the user’s disk encryption password.
The “Self-Encryption Deception” Explained
Two researchers from Radboud University, Carlo Meijer and Bernard van Gastel, analyzed the hardware full-disk encryption of several SSDs by reverse engineering their firmware. That’s how they discovered that hardware implementations have “critical security weaknesses”. These weaknesses are located in many models and allow for complete recovery of the data without knowledge of any secret, their report, titled ‘Self-encrypting deception: weaknesses in the encryption of solid state drives (SSDs)‘, says.
It should be noted that:
BitLocker, the encryption software built into Microsoft Windows will rely exclusively on hardware full-disk encryption if the SSD advertises support for it. Thus, for these drives, data protected by BitLocker is also compromised.
It is also important to highlight that the discovered flaws only affect SSD models that support hardware-based encryption, where the disk encryption operations are carried out via a local built-in chip, which is not connected to the main CPU. These devices are also known as self-encrypting drives (SEDs). They have become quite widespread lately, especially after software-level full disk encryption was proven vulnerable to attacks that led to the theft of the encryption password from the computer’s RAM.
The vulnerabilities affect the so-called “ATA security” and “TCG Opal,” two specifications for the implementation of hardware-based encryption.
The Opal Storage Specification, for instance, is a set of specifications for features of data storage devices (such as disk drives) that enhance their security. The specification defines a way of encrypting the stored data so that an unauthorized person who gains possession of the device cannot see the data.
According to the researchers, the analyzed SEDs enabled users to set a password that served to decrypt their data. However, the devices were also equipped with support for a master password, set by the SED vendor. This is the moment to mention that an intruder who is acquainted with an SED’s manual can easily deploy the master password to obtain access to the user’s encrypted password, thus bypassing the user’s custom password. This can be fixed by changing the master password by configuring the SED’s Master Password Capability to “maximum”.
Another issue uncovered by the scholars concerns the improper implementations of the ATA and TCG Opal specifications. It appears that the user-chosen password and the disk encryption key (shortly DEK) weren’t cryptographically linked:
“Absence of this property is catastrophic. Indeed, the protection of the user data then no longer depends on secrets. All the information required to recover the user data is stored on the drive itself and can be retrieved.”
It’s also crucial to outline that the researchers only tested their findings on a limited number of devices:
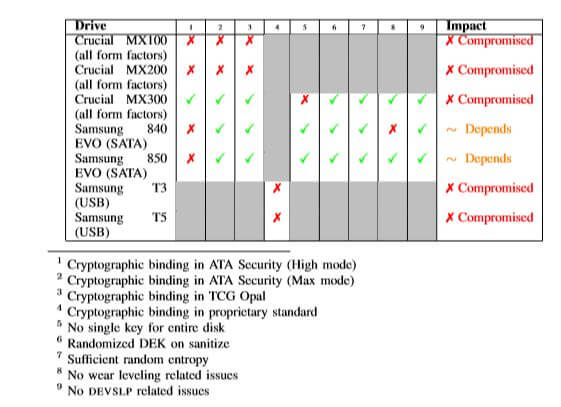
Both internal and external (portable USB-based) SSDs with support for hardware-based encryption were tested. It’s also highly likely that models from a range of vendors are vulnerable as well.
Crucial (Micron) and Samsung already released firmware updates that address these weaknesses.



