Nothing embodies the evolution of digital crime quite like crimeware-as-a-service. Years ago, bad actors preyed upon unsuspecting users by relying mainly on their technical acumen. Sure, they could share their techniques on IRC forums, but it was ultimately up to the individual attacker to code and debug their malicious programs. No one was going to do it for them.
Today, malware developers are still out there. But not every attacker is a programmer. There are some bad actors with low levels of technical expertise. Those individuals would much rather help distribute someone else’s program… just as long as they get to keep some of the spoils of their attack campaigns.
That preference has given rise to crimeware-as-a-service, a model under which anyone can purchase a license to a digital attack tool. Those programs often come with a web interface that allows affiliates to customize their campaigns’ targets and pretexts. At the conclusion of each license period, the license-holders get to keep a share of the profits, whereas a fraction also goes to the original developer. Some licenses expire after just 30 days. Others last a lifetime.
Scamming as a Service
The security community has seen crimeware-as-a-service take the form of ransomware and remote access Trojans (RATs). It’s now come across another iteration of the underground affiliate model: Scam in a Box.
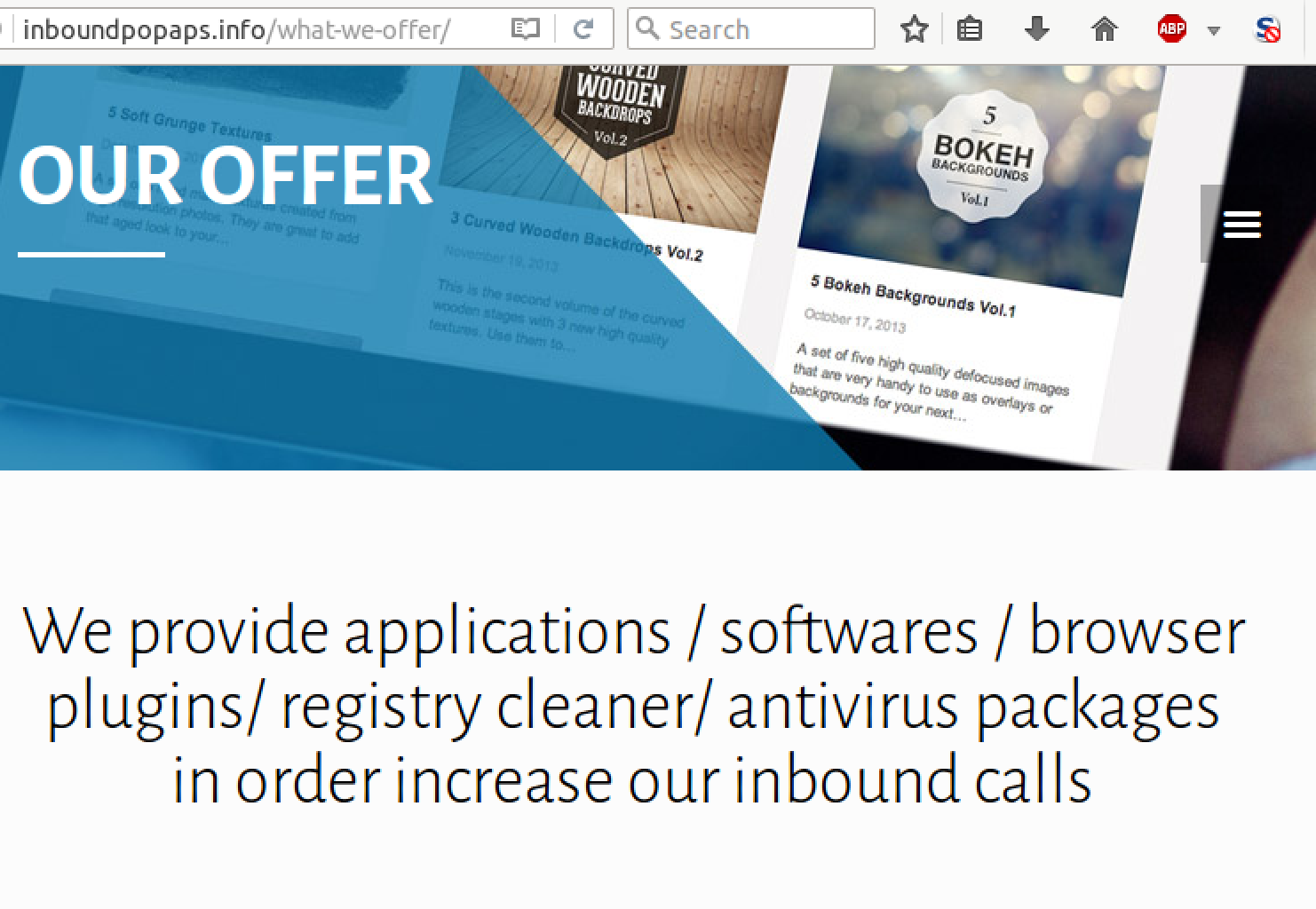
Scam in a Box refers to a service through which criminals with low technical expertise can purchase the infrastructure, troubleshooting, and maintenance necessary to perpetrate a convincing scam online. For instance, one service called Inboundpopaps says it provides “applications,” “registry cleaners,” and “anti-virus packages.” to increase inbound calls.
The long and short of it? William Tsing of Malwarebytes explains:
Pretty cut and dry. ‘We provide malicious software for fraudulent purposes.’ Also notice the admission that PUPs and tech support scams go hand in hand. For more on this connection, see Pieter’s post here. Inboundpopaps is considerably more slick than most scams on the market, and even attempts to limit traffic to real, paying customers.
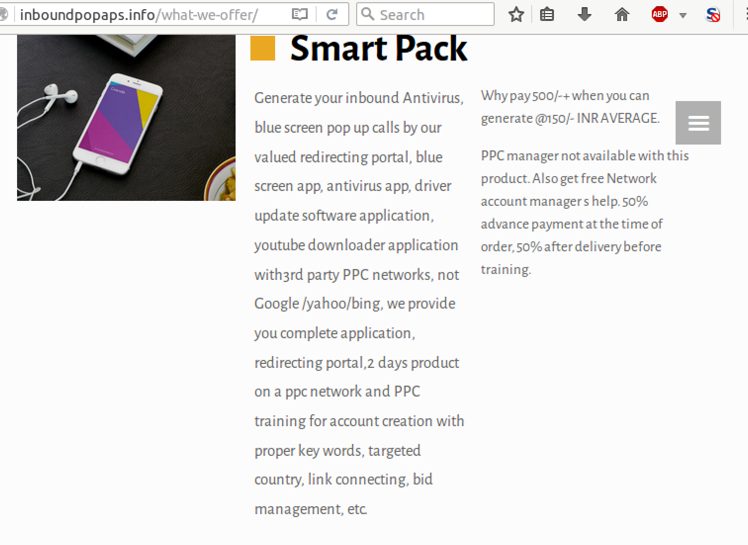
Inboundpopaps offers several different products to buyers. One service called “Smart Pack” helps criminals create their own “antivirus, blue screen pop up calls,” In other words, customers can use the offering to create their own tech support scam.
Smart Pack comes with an app, a redirecting portal, and even pay-per-click (PPC) training on the use of proper keywords and geolocation.
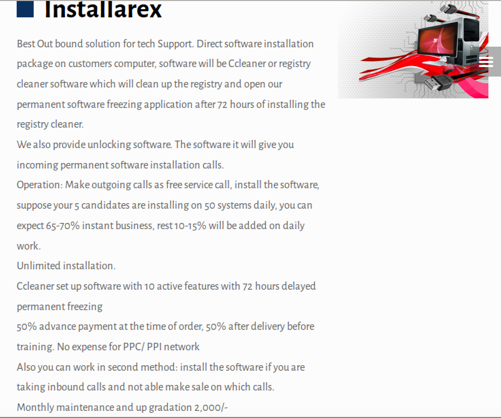
Another service, “Installarex,” is software that mimics a registry cleaner. But that’s not really what it is. It’s actually a screen locker that activates 72 hours after installation.
50 percent of the service’s cost is due at the time of purchase, while the rest comes after delivery and before training. Once that amount is paid, criminals can do whatever they want with it. That includes “install[ing] the software if you are taking inbound calls and not able make sale on which calls.”
Clearly, the developers have thought out how Smart Pack, Installarex, and their other services can be bundled together.
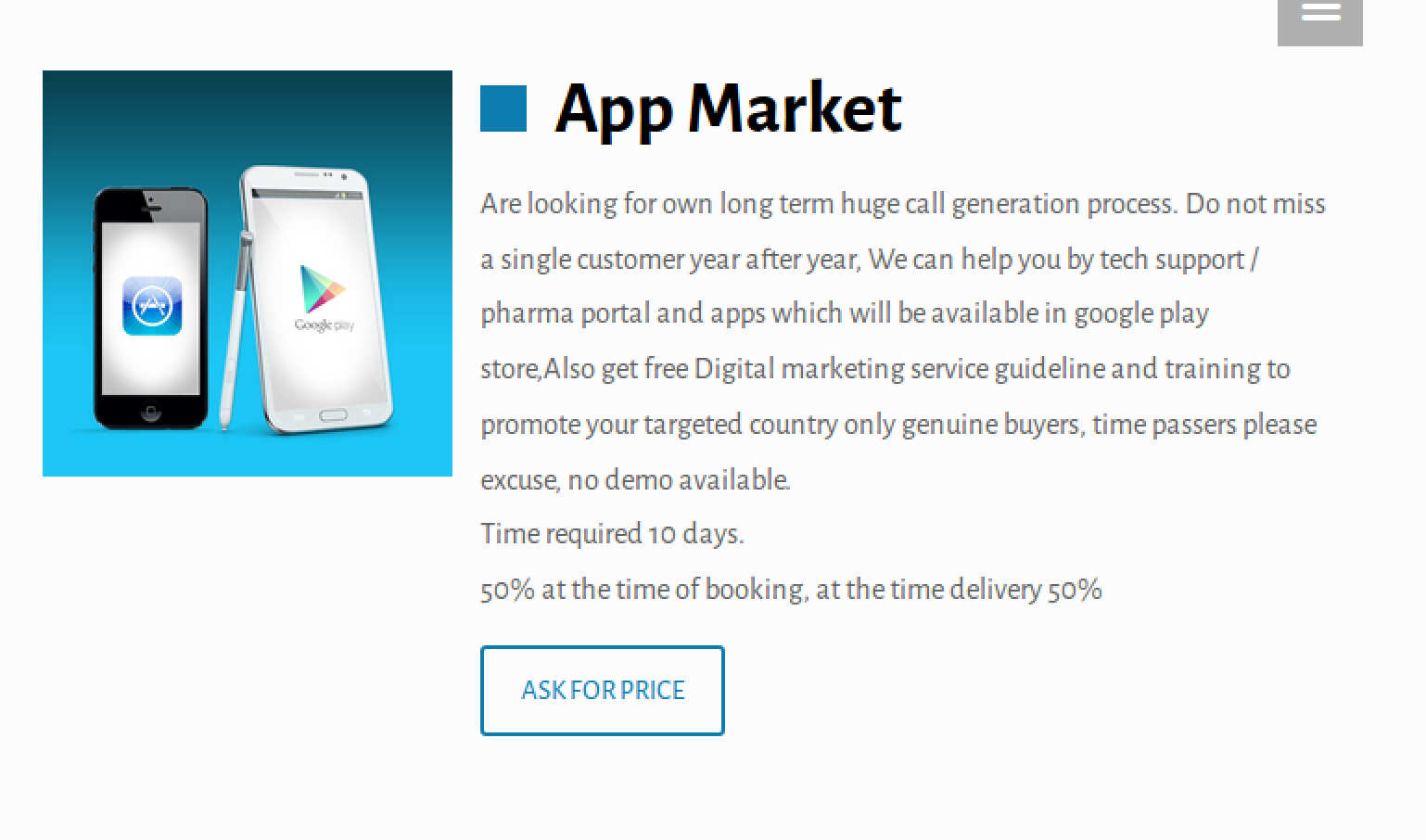
Last but not least is App Market. Tsing weighs in on the product:
…[W]e see offers for fake mobile apps, along with training on how to sneak them into assorted app stores. This is intriguing as mobile tech support scams aren’t extremely common. Unfortunately, as much as we’d love to “Ask For Price”, that link simply reloads the page. The blurb for windows lockers quotes the monthly maintenance as 2000 IND per month, which equates to about $30 USD. Given that price is for one of the more resource intensive scams, one might presume the others are even cheaper.
Conclusion
Scam in a Box solutions like those offered by Inboundpopaps make it easy for criminals with low levels of technical expertise to perpetrate a scam. As a result, it would be foolish of us to think scams will be going away anytime soon. Which is why users need to protect themselves against some of the most common scams. They can do so by installing an ad-blocker and by downloading legitimate software directly from vendors’ sites and not from sketchy third-party marketplaces.
Editor’s Note:
From time to time, SensorsTechForum features guest articles by cyber security and infosec leaders and enthusiasts such as this post. The opinions expressed in these guest posts, however, are entirely those of the contributing author, and may not reflect those of SensorsTechForum.