2017 was a year of increasing menace for ransomware, its first real breakthrough year found it on the front-pages of mainstream media as well as highbrow IT publications. The rapid ascension of WannaCry, GoldenEye, NotPetya led to heightened apprehension and vigilance from IT managers and business owners across the planet.
Its sudden prominence is a mouthwatering proposition to cybercriminals – it has managed to develop its own economy: low barrier to entry, small investment, high rewards, and even its own business model. A sophisticated network complete with supply-chains, creators, distributors, marketplaces, DIY kits, affiliate contracts, adverts and some would argue its own currency.
Studies have shown that that ransomware has seen a 2500% rise since 2016, with over 6300 marketplaces and nearly 45000 product listings. The total market value estimates have totaled out at almost $1 Billion.
Ransomware: The Business Model
The rise of ransomware is hinged on fairly simple business principles; notably, supply meeting demand, low barrier to entry, low capital investment, easy scalability, and a large market to target.
The world’s environment was rife for a cyber threat like ransomware; much of its rise comes down to advancing technology and sheer opportunity. We now live in an increasingly online world, our phones and laptops hold some of our most sensitive and personal information, likewise, businesses often hold their entire businesses on servers with no backups. Everyone is now a mark, exacerbated often by lax security and poor employee training.
The days of ransomware and viruses being only for sophisticated hackers are long gone. Ransomware-as-a-Service has seen to this; RaaS is a completely turnkey solution enabling anyone to participate in these illicit activities, with no coding experience or technical skills, if you can navigate the dark web you can join in on ransomware campaigns, even with no capital investment.
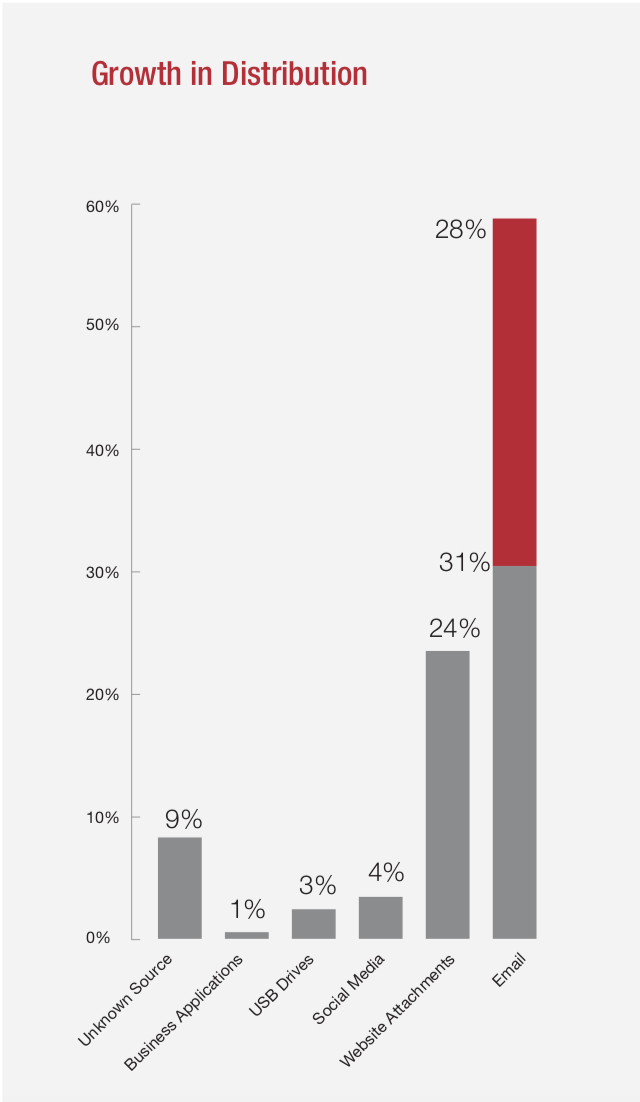
It can be sent for free: р-mail, which is still the most common means of ransomware infection allowed criminals to distribute ransomware to 100,000s or even millions of people in one blast. We are also moving into a world in which not only is everyone a mark but everything: IoT could lead to everything from cars to fridges being held to ransom.
Anonymous criminals: Faceless criminals, utilizing the Tor network and leveraging crypto payments can maintain their anonymity – if you are a small business or individual the chances of you catching the criminal are slim to none.
According to Carbon Black, the ransomware marketplace has grown from $250,000 to over $6,000,000 in the past year – much of this growth is down to RaaS. DIY kits often a menu of ransomware at various price points, custom ransomware builds can cost you up to $3,000 but clones and DIY kits can cost less than a dollar.
The Ransomware Supply Chain
Creation: This is the nerve center, where the sophistication and real expertise come in. Author’s and coders develop ransomware programs that can be placed on marketplaces, sold, or leveraged by RaaS software.
Distribution: This can be a direct sale or places on RaaS platforms. On distribution, authors will either take a cut of ransoms OR be paid upfront. The cost is dependent on how customized the code is, this usually correlates with its ability to go unnoticed by anti-viruses and spam filters. Distributors can also buy “shares” in a campaign, where the proceeds are split depending on the investment. The viruses themselves are usually sent out as ‘spray-and-pray’ spam mail lists or specifically targeted hacks that exploit vulnerabilities.
Encryption: There are generally two types of ransomware encryption, the first is the so-called locker ransomware and the second is crypto.
The locker is the oldest form of ransomware, which stops user interaction with a computer usually within the browser. These ransomware pieces often mimic government agencies, using social engineering tactics to coerce money from frightened users.
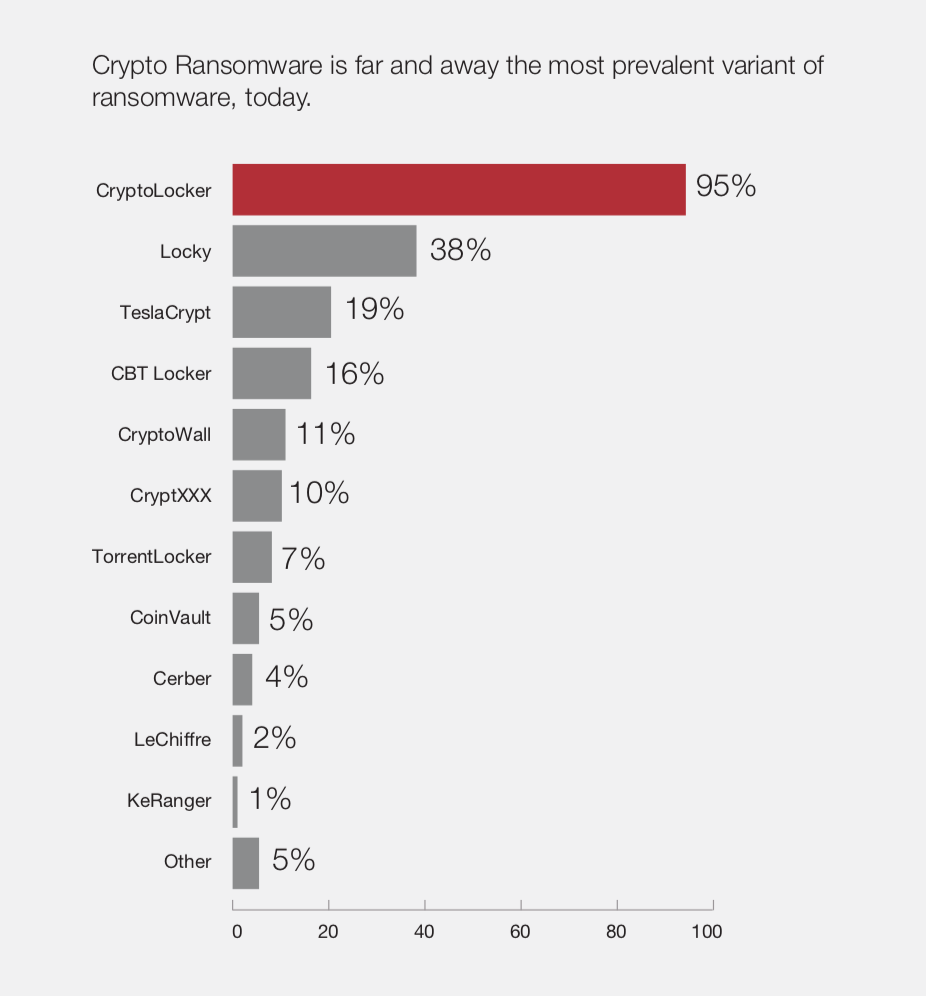
Crypto ransomware is the variety that we are seeing more and more often, this involves encrypting valuable information stored on computers, making the data unusable unless it is unencrypted. WannaCry and NotPetya were both crypto ransomware.
Payment: The most important part of the ransomware puzzle and one would think the easiest. Typically a bitcoin wallet key is generated or posted on a website, an easy way for anonymous payment. However, it’s not all plain sailing Instances of wrong wallet keys being placed or wallet keys being blocked are common. WannaCry which developed a way of generating unique Bitcoin keys (unblockable), had a fairly easy kill-switch which stopped its spread.
Decryption: And alas, the funnel is completed – once payment is received the code to decrypt your files are sent. Ultimately however by paying the ransom, you are only encouraging this type of activity to continue.
2017 saw an increase in Ransomware at scale, more money, more marks, more attacks, and more profile. However, many of the attacks still made rookie errors – these errors will in all likelihood not be ironed out in the future. IoT and the stratification of everything from phones to fridges will see 20.4 billion devices internet-connected 2020 – only increasing our susceptibility to attack.
Editor’s Note:
From time to time, SensorsTechForum features guest articles by cybersecurity and infosec leaders and enthusiasts such as this post. The opinions expressed in these guest posts, however, are entirely those of the contributing author, and may not reflect those of SensorsTechForum.