Computer criminals constantly attempt to break in to user and company devices and networks. And while this process may seem like wizardry, in most cases they actually use sophisticated software and code. Our article aims to showcase the most popular hacking tools in 2017 as used by computer criminals around the world.
1. Metasploit
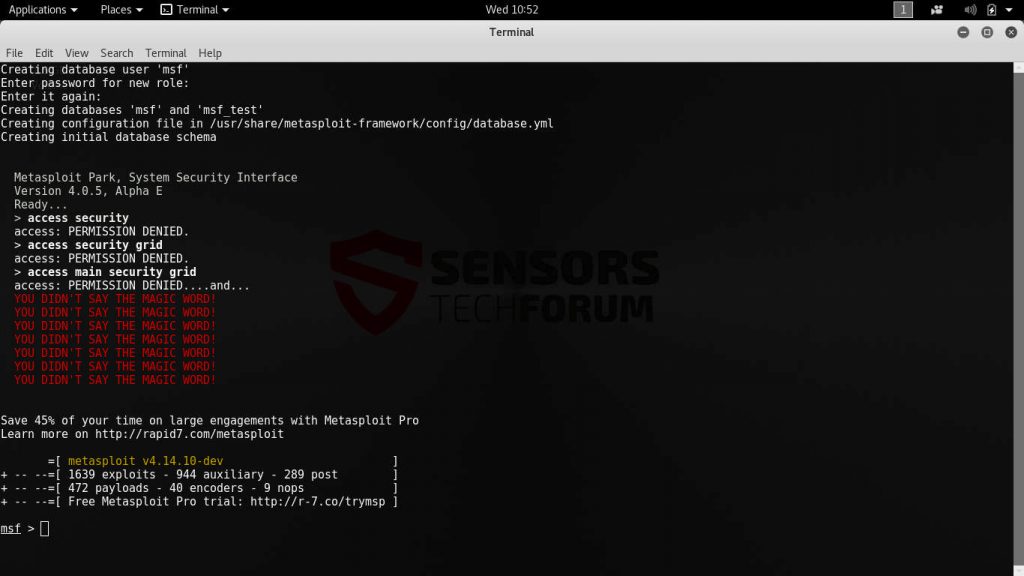
Metasploit is the de facto standard hacking tool when it comes to performing vulnerability assessment. This is one of the most feature rich platforms that allows even beginner criminals to launch sophisticated attacks using short commands. By far this is one of the most popular suites when it comes to teaching both security professionals and hackers about vulnerability scanning and penetration testing.
It is available in several editions (free and paid versions are available) and depending on the configuration and goals it can be used in different ways. Metasploit is comprised of a flexible framework that allows its operators to launch exploits and payloads. The modular approach can be used to launch well-known attacks, as well as custom code against whole networks. The framework is typically used in conjunction with other network security tools to conduct a preliminary analysis of the intended targets.
Once the criminals know what operating system, device and services are running, they can use Metasploit to launch hacking attacks and break into the system. Depending on the version and configuration the available tools can include any of the following:
command line or graphical interfaces, third-party import of exploits, manual/automatic brute force, network discovery, evidence collection, social engineering campaigns, web applications testing and VPN tunneling.
Metasploit contains one of the largest collections of exploits available for both applications, operating systems, dedicated devices or multi-platform injections. It can be extended by plug-ins or third-party modules if the core functionality is limiting. Using it in live hacker attacks the operators can institute a wide variety of infection types: from overtaking the devices to spying on the users in real time and stealing sensitive information and credentials. In comparison with other similar platforms Metasploit contains post exploitation capabilities as well. This is a very important step when it comes to sensitive data collection and deep infections.
The framework has been used to launch dangerous persistent installations – viruses and malware that attach themselves deep in the computer settings and cannot be removed by using any manual methods. Only the use of a quality anti-spyware solution can remedy them.
2. Wireshark
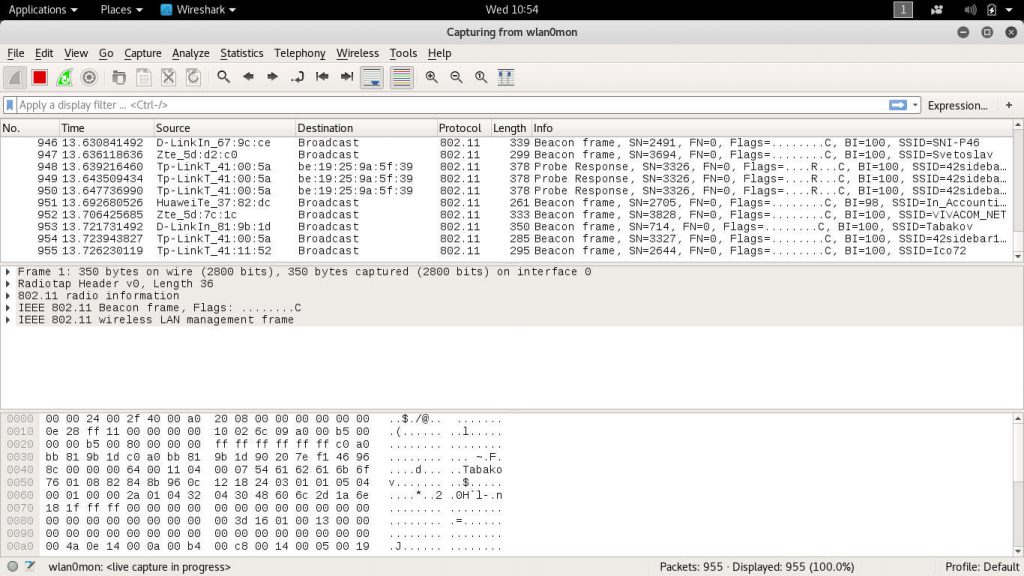
Wireshark is probably one of the most widely used tool both by security and network administrators and computer criminals. It is a multi-platform network protocol analyzer that allows its users to capture data from a wide variety of network sources – Wi-fi networks, Bluetooth, wired connections and etc. It can be used to live record the data or analyze it offline for further inspection.
One of the reasons why Wireshark is so useful is that it supports practically all capture file formats used in the industry. The application is compatible with virtually all popular devices and operating systems. In addition it supports decryption of many protocols and all results can be exported to further formats for storage and analysis.
A Wireshark session is usually started in the following sequence:
- Start the application with the required privileges to load network traffic.
- Configure the interface options by specifying which interface is going to be used for the traffic capture and engage the process.
- Use the available plugins, filters and scripts to show the data stream.
- The extracted data can be exported to other standart formats for further analysis if that is required.
The protocol analyzer works using display filters, plugins and scripts. Popular tutorials on the Internet and ready-made instructions can be used to troubleshoot network issues and security-related incidents. Wireshark is useful in scanning for virus attacks by looking up for malicious endpoints and strings associated with ransomware and Trojans.
3. Nmap
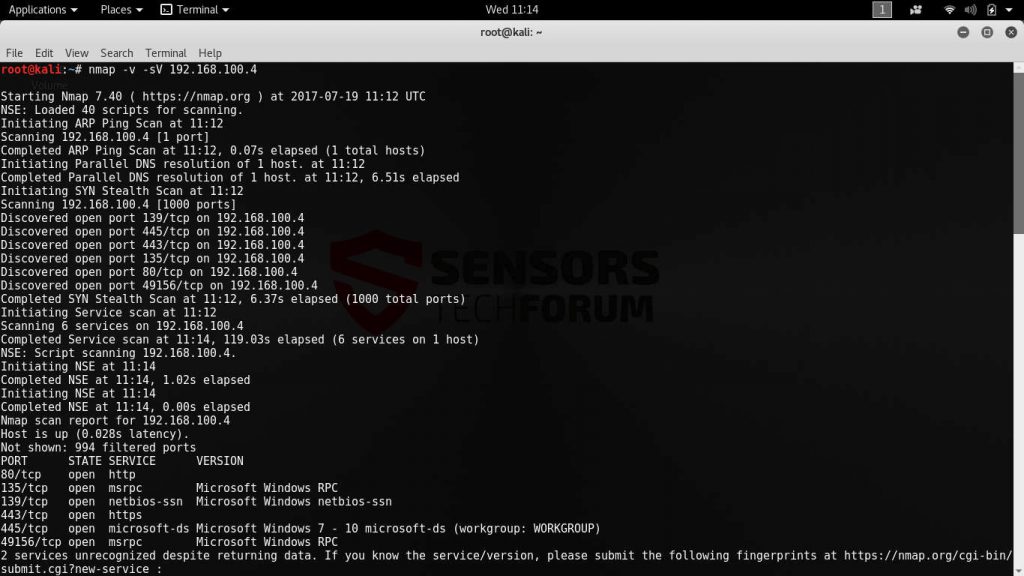
Nmap (short for “Network Mapper”) is a versatile and powerful tool used for network discovery and security audit. Network administrators can use it to create a detailed report of all available devices on the connected networks, monitor uptime or discover online services.
The utility has many features including raw packets identification, service detection and one of the best operating system fingerprint detection databases. Nmap is capable of identifying both the version of the running systems, but also all server applications.
Using a single command the administrators can query a wide array of detailed network data on whole computer networks. The developers maintain binary packages for the most popular operating systems – Gnu/Linux, Microsoft Windows and Mac OS X.
Part of the security suite that is related to Nmap also includes the following applications:
- Zenmap – a powerful graphical user interface to Nmap.
- Ncat – a very powerful data transfer and debugging tool.
- Ndiff – results comparison tool.
- Nping – packet generation and response analyst tool.
The application is able to overcome certain anti-hacking security tools. Even when such filtered ports and other defense mechanisms are used, the utility can use an advanced scanning mechanism to showcase the available device and services.
Nmap is also famed for its scripting engine called NSE (Nmap Scripting Engine). It allows the users to write, share and execute scripts written in the Lua programming language. Using ready made commands the majority of routine network security tasks can be automated.
The extensive features available for Nmap allow its operators to evade firewalls and intrusion detection systems, as well as spoof devices and imitate application protocols. Depending on the individual cases the penetration testers can utilize different tactics in their hacking campaigns.
4. John the Ripper
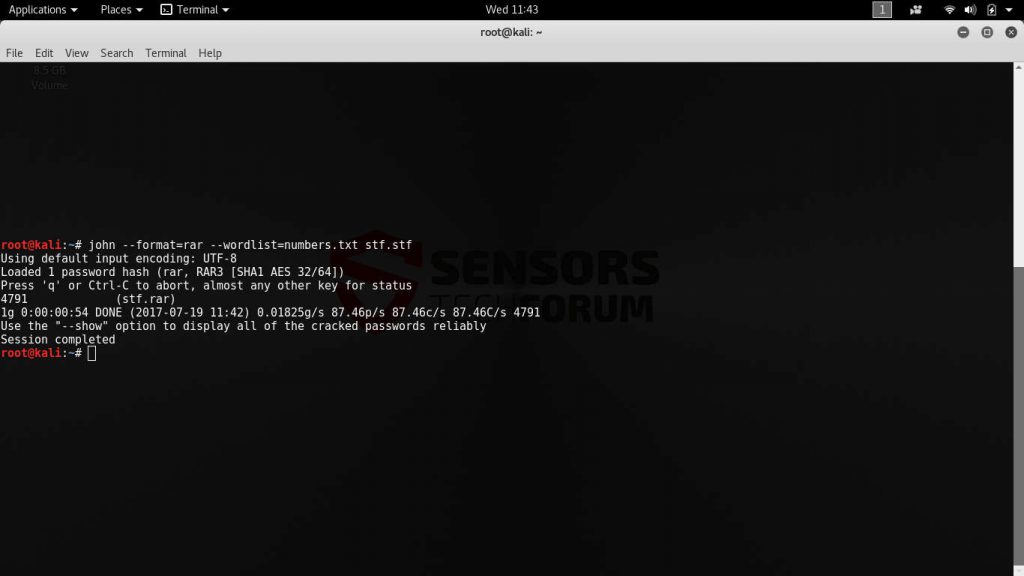
John the Ripper is probably the most famous password cracker. The applications is compatible with the most popular operating systems and can be used to break all kinds of passwords. Hacking different types of data is easily achieved using crackers like this one.
The primary aim of the application is to detect and recover weak Unix passwords. However due to the wide availability of features and the smart algorithm integrated into the code, John the Ripper has become a standard tool for breaking common ciphers.
John can be used by supplying the program with a password file. Optional parameters include the cracking mode and specific performance-related settings. Wordlist files can also be fine tuned to mangle the words, eliminate duplicate candidate passwords, assign certain length and etc. The following hash types are supported out of the box:
Traditional DES-based, SHA-crypt, SunMD5, NTML and Mac OS X salted SHA1-hashes, “bigcrypt”, BSDI extended DES-based, FreeBSD MD5-based, OpenBSD Blowfish-based, Kerberos/AFS, Windows LM and DES-based tripcodes.
Ready-made editions can also be used to crack passwords used by database servers, network authentication servers, IRC bots, services, remote desktop protocols, PDF files, archives and other sensitive data and services.
The password cracking engine can be used to perform intrusions in situations where vulnerabilities cannot be detected. Using this approach hackers can break into systems where an additional layer of authentication or another security feature has not been implemented.
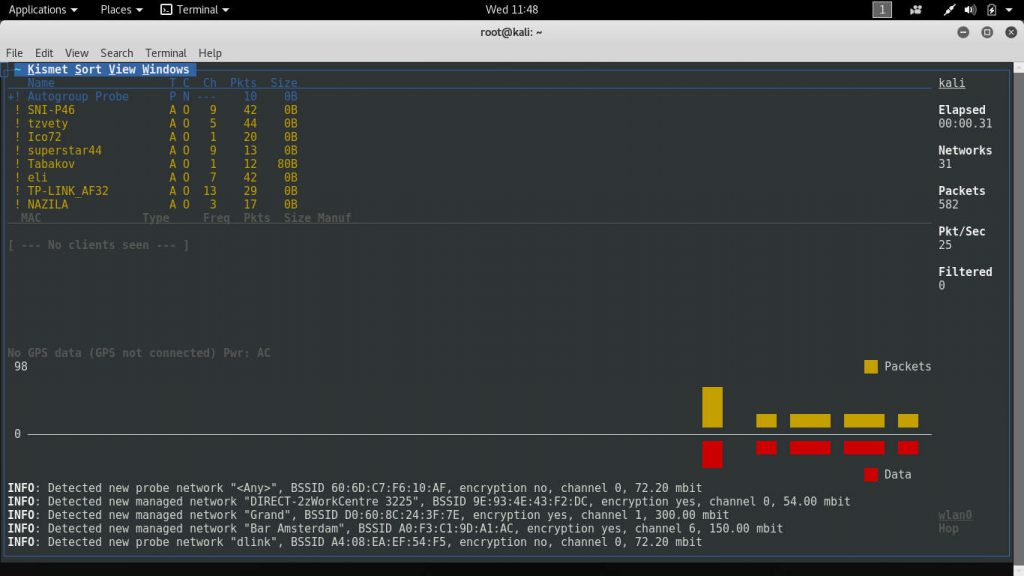
5. Kismet
This is a console-based wireless network detector with advanced features. It can be used to identify networks in range by using passive scanning as opposed to other approaches. This gives it the advantage of being able to detect hidden networks even if they are not in use and do not transmit the usual beacons.
Other features include the following:
- Automatic detection of network IP blocks by analyzing the sent TCP, UDP, ARP and DHCP packets.
- It can log the traffic in a Wireshark compatible format that can be analyzed by the application.
- If a GPS device is configured and connected to the device Kismet can automatically plot the detected networks and estimate the ranges on a map.
- Kismet can be expanded using plugins to enable additional commands.
- It operates using a client-server model which allows it to be executed under flexible conditions.
- Multiple capture source is supported.
Computer criminals use Kismet when performing wardriving hacking attacks. This is the well-known practice of scanning and plotting Wi-Fi networks using laptop computers or smartphones. Kismet is used as a first-stage reconnaissance tactic to query the available networks of a particular location.
Users of the utility can enable and use basic and advanced filtering to gain information on the target networks. The built-in engine the app can also be used to alert the operators about certain characteristics and any unusual probes, floods and other indications. Its ability to act as a potent intrusion detection system can be utilized to watch out for any unusual events. Together with the traffic data gathered and analyzed in Wireshark, the hacker operators can gain a detailed perspective of the Wi-Fi networks in range.
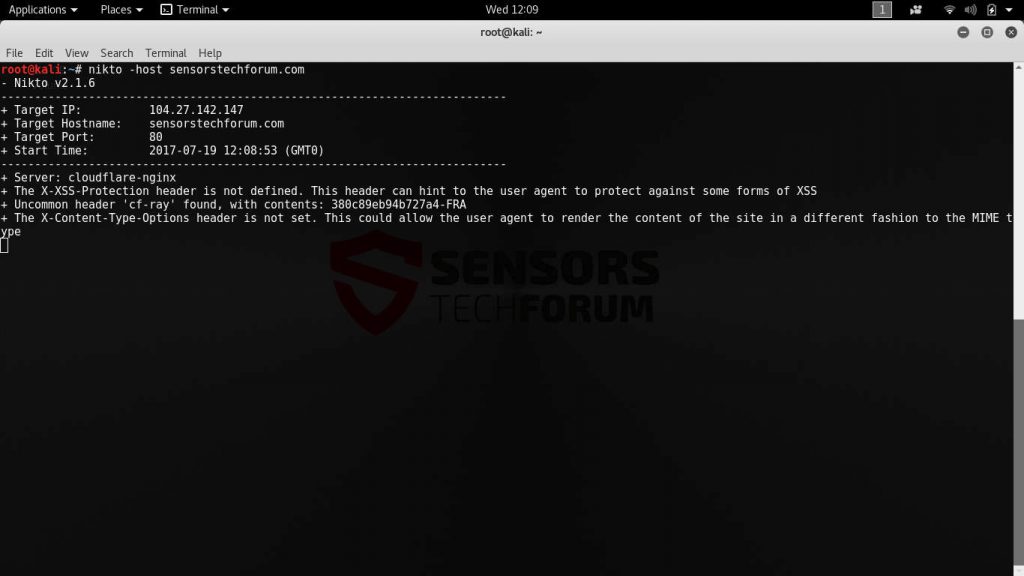
6. Nikto
Nikto is a powerful web server scanner that is able to perform extensive tests on target machines. The application is able to create a security audit on the intended targets by launching an array of assessment tests. It is designed to identify default and insecure installation, configuration parameters and running services on the target web servers. Penetration testers and computer criminals can use it to find potential vulnerabilities in the target systems.
Nikto can run on every platform that supports the Perl environment – from ordinary laptops and desktops to board computers and mobile devices. The engine supports proxies, SSL connections, host authentication methods, attack encoding and other features. Its interface is very easy to use it as it uses a logical and easy to use command-line syntax.
The utility can be used as a first point of analysis of certain web addresses as it is able to identify the running services using several different methods for better accuracy. If configured the web scanner is also able to map out the domains and utilize subdomain guessing to give further insight into the setup. To facilitate a complete security audit Nikto can log all results and output to the Metasploit framework. Nikto is one of the top choices when hacking target hosts.
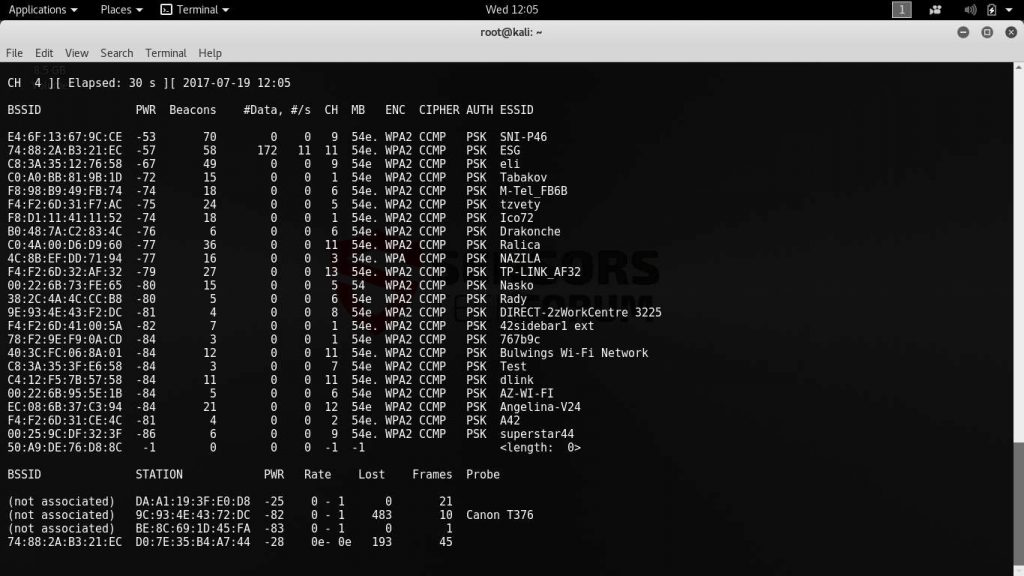
7. The Aircrack Suite
Aircrack is a suite of tools for hacking wireless networks. It is comprised of several applications that are used in conjunction with each other.
They can be used both for manipulating data streams, crafting packets and analyzing the captured network traffic. In comparison with other tools on this list it requires more manual intervention and is designed for more technical users and system administrators. However it is a really powerful tools in the hands of the adept security engineer or criminal as the applications provide a nearly unlimited array of launching all sorts of attacks. The complete Aircrack suite includes the following tools:
- aircrack-ng – This is the main application that can crack WEP passwords using several different methods. The software allow for dictionary attacks and other methods when such actions are done against the more complex WPA2-PSK protected networks.
- airdecap-ng This program decrypts WEP/WPA encrypted files using a known key.
- airmon-ng – The execution of this app places the different card in monitor mode.
- aireplay-ng – This is a packet injector that can be used to craft malicious packets. Such software can be used to exploit discovered vulnerabilities.
- airodump-ng – A packet sniffer that is able to collect network traffic data and export it in either pcap or IVS standard files.
- airtun-ng – A virtual tunnel interface creator.
- packetforge-ng – A packet injector similar to aireplay-ng that crafts encrypted data instead of plaintext.
- ivstools – Utility used to merge and convert recoreded packet data.
- airbase-ng – This tool allows for the coordination of techniques to attack individual hosts.
- airdecloak-ng – Modifies PCAP captured data by removing recorded WEP cloaking.
- airolib-ng – This part of the Aircrack suite is used to store and manage the ESSID network names and passwords. It also generates Pairwise master keys.
- airserv-ng – Airserv allows the operators to access the configured wireless cards from other computers.
- easside-ng – Aircrack utility that allows for access point communication without a WEP security key.
- easside-ng – A helper application that communicates with easside-ng when run on a remote host.
- tkiptun-ng – WPA/TKIP encryption attack tool.
- wesside-ng – A hacking tool that automates WEP security key recovery.
As such the Aircrack suite can be used for all essential penetration testing scenarios: network data monitoring, conducting attacks and assessing the security level, testing Wi-Fi adapters and cracking discovered passwords. Like Nmap the apps rely on a command-line interface that is suitable for scripting use. The operators can automate tasks by creating scripts that utilize several tools in a logical command chain.
8. THC-Hydra
THC-Hydra is an optimized network cracker. It supports many different services and thanks to its wide feature set and service compatibility THC-Hydra (or simply Hydra) it is one of the most widely used utilities when it comes to hacking network devices.
Hydra works with a wide range of protocols, services and applications protected by passwords. The latest version can act against the following targets:
Asterisk, AFP, Cisco AAA, Cisco auth, Cisco enable, CVS, Firebird, FTP, HTTP-FORM-GET, HTTP-FORM-POST, HTTP-GET, HTTP-HEAD, HTTP-POST, HTTP-PROXY, HTTPS-FORM-GET, HTTPS-FORM-POST, HTTPS-GET, HTTPS-POST, HTTPS-HEAD,
HTTP-Proxy, ICQ, IMAP, IRC, LDAP, MS-SQL, MYSQL, NCP, NNTP, Oracle Listener, Oracle SID, Oracle, PC-Anywhere, PCNFS, POP3, POSTGRES, RDP, Rexec, Rlogin, Rsh, RTSP, S7-300, SAP/R3, SIP, SMB, SMTP, SMTP Enum, SNMP, SOCKS5, SSH (v1 and v2), Subversion, Teamspeak (TS2), Telnet, VMware-Auth, VNC and XMPP.
The most popular web protocols (HTTP, POP3, IMAP and SMTP) are fully supported with several login mechanisms used for authentication – plaintext credentials, MD5 digests, hashes and etc. The application uses a simple graphical user interface (GUI) that allows even inexperienced users to launch hacking attacks.
The cracking attempts can be routed over several type of proxy server for privacy reasons. And when compared with other similar password crackers THC-Hydra shows that it has one of the most extensive feature lists and capabilities. It has grown into a preferred method of launching intrusion attempts as it supports services often used in corporate environments – Oracle databases, Active Directory protocols, email and web services, remote desktop sessions and more.
9. The Social-Engineer Toolkit
The Social-Engineer Toolkit is a popular open-source framework that is designed to launch exploits and social engineering attacks. The utility provides a very easy to use command-line interface and supports custom attack vectors. Like Metasploit it features a modular engine that allows programmers to create custom code that can be adapted to specific scenarios.
By default the malicious engine allows for the coordination of the following types of network attacks:
- Spear-Phishing Attacks – They constitute one of the most popular social engineering scams sent to potential victims. The targets receive messages that appear as being sent by legitimate institutions, usually by e-mail, social networks or instant messaging services. The most popular examples include posing as PayPal, Google or other famous and widely used Internet companies. The victims are redirected to sites that appear as login pages or service home pages where they are asked to enter their account credentials. Other case include adding malware as file attachments or hyperlinks.
- Website Attacks – The Social-Engineer Toolkit includes an engine capable of conducting potent attacks to attempt hacker intrusions into the targets. The framework allows its operators to launch multiple attacks at once to increase the success ratio.
- Infectious Media Generator – This function allows the criminals to create a malicious payload that can be used to infect victim systems.
- Mass Mailer Attack – The attack allows the hacker operators to setup and coordinate spam messages and other similar campaigns.
- Create a Payload and Listener – It uses the Metasploit farmework to generate a binary file that has to be installed on the victim machines. Once in place it is used to “listen” to the machines.
- Arduino-Based Attack Vector – These types of attacks can overtake Arduino-based devices and reprogram their code. They are usually used in many IoT (Internet of Things) products, as well as DIY hobby projects.
- SMS Spoofing Attack Vector – This option allows the criminal operators to spoof phone numbers and send SMS messages. Such attacks are useful in the process of running a social engineering campaign in combination with other attacks such as credentials harvesters. The Social-Engineer Toolkit can utilize ready-made templates and perform mass SMS message sending at once.
- Wireless Access Point Attack Vector – One of the most popular mechanisms of hacking devices is by spawning a malicious wireless access point and using the DNS spoofing attack to make the devices connect to the rogue network. When this is done another attack can be initiated to infect them. As soon as the connection is made all generated traffic can be spied upon by the hackers. Such attacks are very useful when conducting identity theft and other related crimes.
- QRCode Generator Attack Vector – Social-Engineer Toolkit includes an engine that is able to generate malicious QR codes. When they are scanned by the targets they are redirected to a crafted hacker-supplied address or an exploit is launched depending on the configuration.
- Powershell Attack Vectors – Automated shell scripts written in PowerShell can be executed on the infected computers when instructed via the menu options.
- Third Party Modules – The Social-Engineer Toolkit can be extended using additional scripts and plugins.
The Social-Engineer Toolkit provides one of the most extensive collection of exploits and attacks. The fact that it contains a lot of built-in options for configuring the infection chain allows the criminals to launch sophisticated campaigns against whole computer networks. In combination with Nmap and other security tools the hackers can achieve a very high probability of infiltrating vulnerable devices and networks.
10. The Tor Project
The Tor network is probably the most famous international anonymous network that is used by computer users who want to protect their security and privacy. Tor routes the network traffic through a series of routers and nodes which makes it very hard to for Internet service providers, service owners and system administrators to locate the point of origin. It is primarily used to combat censorship however it has grown to be an essential part of every hacker toolkit.
The criminals route their activities and attacks through the network to hide their true origins and abuse the network’s capabilities frequently by operating hacker underground markets and chats on the hidden network. The majority of operations are actually planned on private forums and communities that are only accessible via the Tor browser. Wannabe criminals frequently “lurk” or browse the underground sites in search of tutorials and instructions for hacking computers and networks.
Conclusion
This article presents some of the best and most widely used hacking tools in 2017. They reflect the current attack trends that are popular in the last few months. The criminals focus on coordinating attack campaigns according to the potential targets. We showcased how the applications can survey and reconnaissance the computer networks and systems in advance, this gives the attackers a distinct advantage of knowing what intrusion attempts to consider.
The flexibility of being able to launch multiple campaigns at once, a sequence or a carefully created script makes it the tools very useful. And while they are the standard for penetration testers worldwide, many of them have gained their reputation as the premier hacking tools. Our article explicitly mentions just some of the possible scenarios.
Note! You can protect yourself from incoming malware infections by using a quality anti-spyware solution.