One of the biggest accounting firms, Deloitte, has been through a critical data breach that has affected its internal email systems. The company has tried to soften the impact of the incident by stating that it affected a handful of their customers.
However, there are sources proving them wrong. According to a particular source, the breach took place in the autumn of 2016 or even earlier. As reported by KrebsOnSecurity, all admin accounts at Deloitte have been compromised, making the breach a serious one.
Deloitte’s Data Breach Affects the Firm’s Top Blue-Chip Clients
Earlier this week, the Guardian was first to report that a breach at the accounting company included the leak of personal information, usernames and passwords on the firm’s top blue-chip clients. As stated by the media:
The Guardian understands Deloitte clients across all of these sectors had material in the company email system that was breached. The companies include household names as well as US government departments. So far, six of Deloitte’s clients have been told their information was ‘impacted’ by the hack.
Later on, in a statement to KrebsOnSecurity, the company confirmed it was compromised by a cyber incident which led to unauthorized access to its email platform. Here’s an excerpt of that statement:
Importantly, the review enabled us to understand precisely what information was at risk and what the hacker actually did and to determine that only very few clients were impacted [and] no disruption has occurred to client businesses, to Deloitte’s ability to continue to serve clients, or to consumers.
Unfortunately, the circumstances surrounding Deloitte’s data breach may be more complicated than the company admits. Internal information shared by an unknown person states that the company is still unaware of the precise time the breach happened, and still has no knowledge of how long the attackers stayed inside the system. The anonymous source also revealed that the team investigating the breach is looking into a company office in Nashville. This is where the incident most likely was triggered.
Deloitte Was Long Aware of the Data Breach
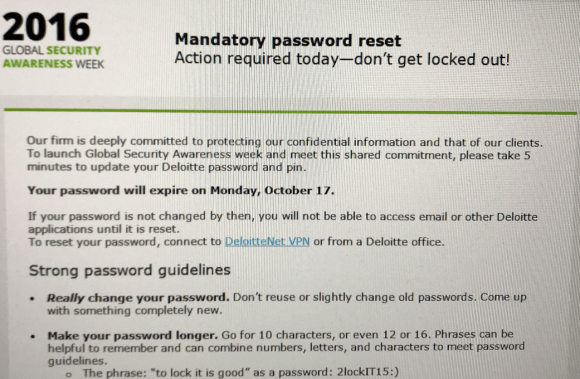
As it seems by putting two and two together, Deloitte was aware that something wasn’t right for some time now but decided to keep quite. In support of that claim, the anonymous source said that the company sent out an email regarding a mandatory password reset on Oct. 13, 2016, almost a year ago. The email was directed to all the company’s employees in the US. The email stated that passwords and PINs needed to be changed by Oct. 17, 2016. If the password/PIN reset wasn’t done accordingly, the employees wouldn’t be able to access their emails or other company apps. This is what the message looked like:
The timing of Deloitte’s breach is quite intriguing considering that another dangerous breach was revealed just recently – the incident at credit reporting company Equifax.
The experts who were investigating the hack stated that the following types of data were extracted: social security numbers (SSN), addresses, date of birth, driver license numbers and payment card details of approximately 209 000 US citizens.
As for the consequences of Deloitte’s hack – the incident is still being investigated, and details are pending.