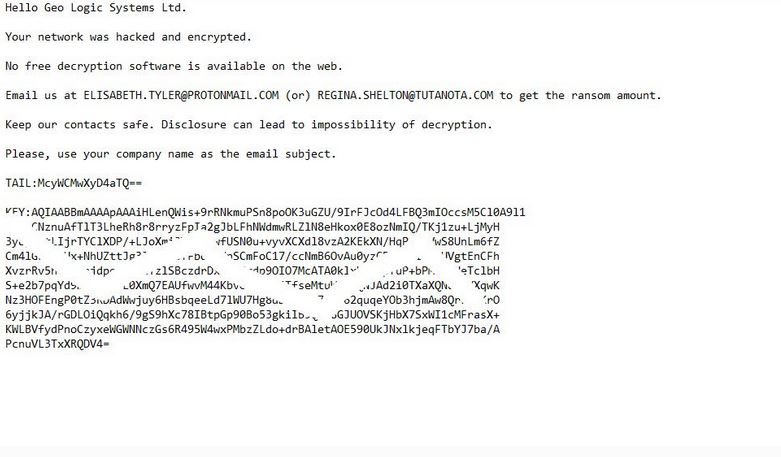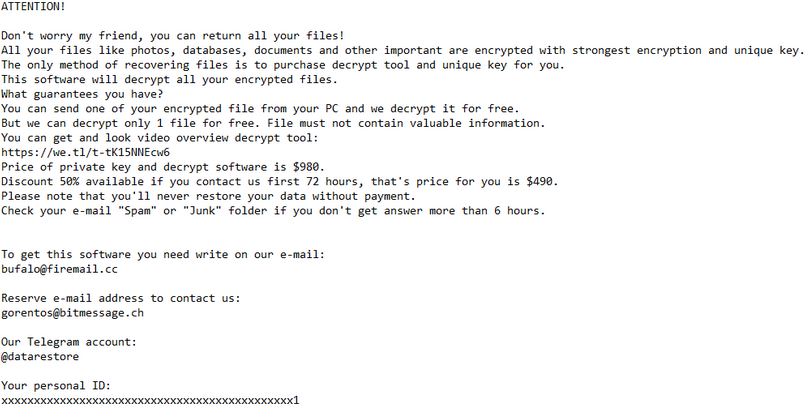
.mogera Ransomware – Remove It + Decrypt Files
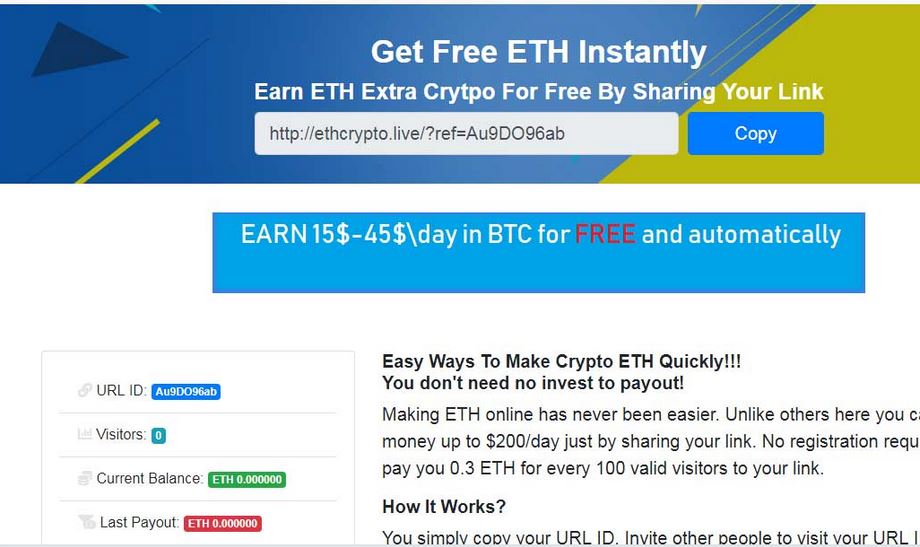
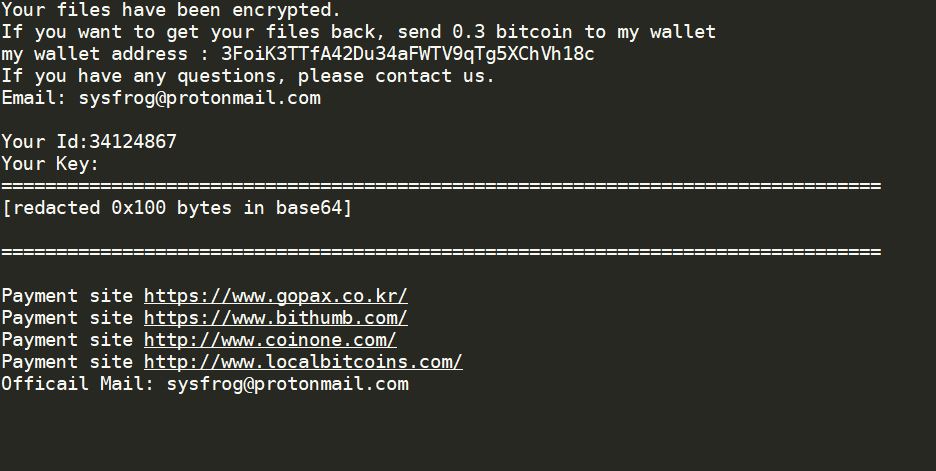
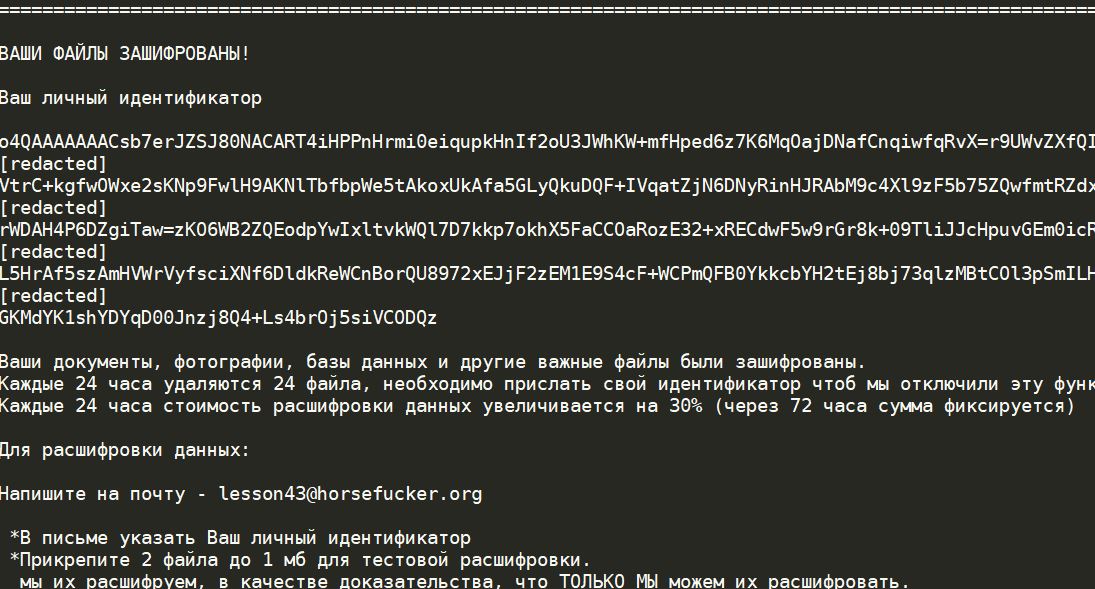
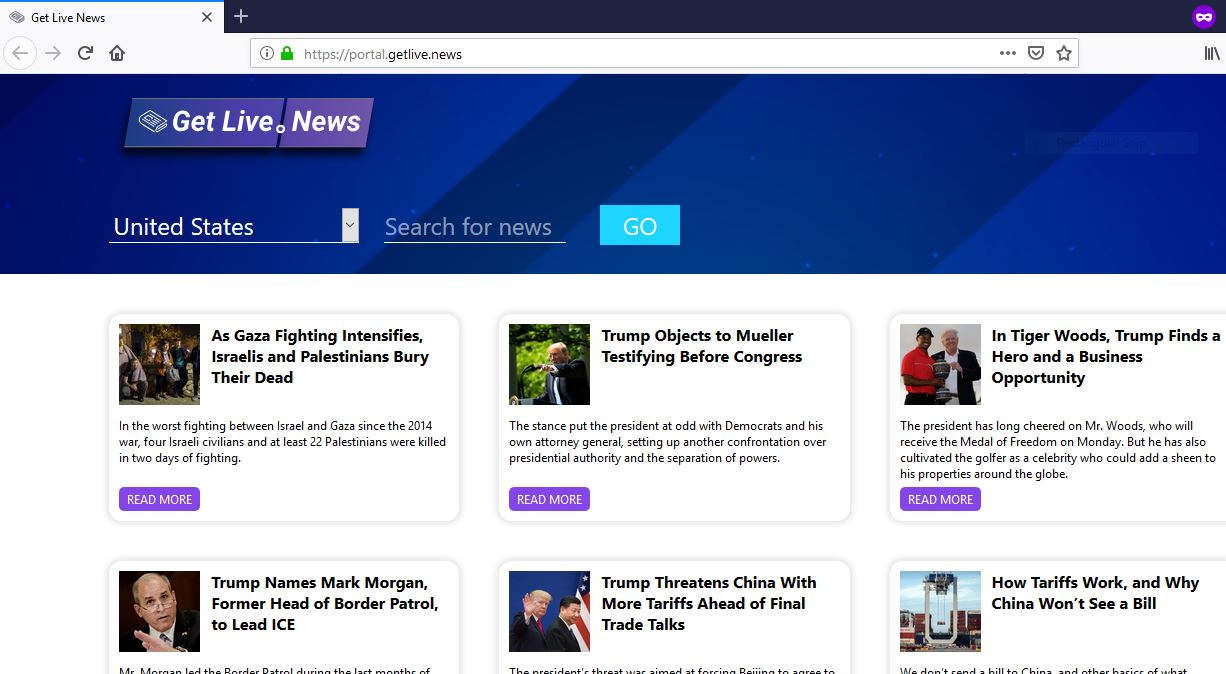
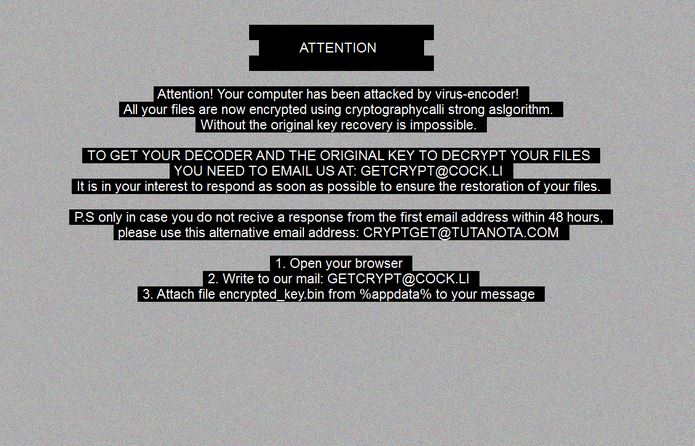
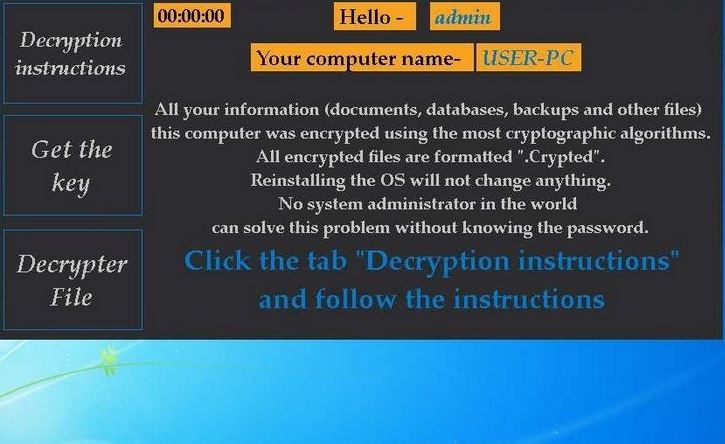
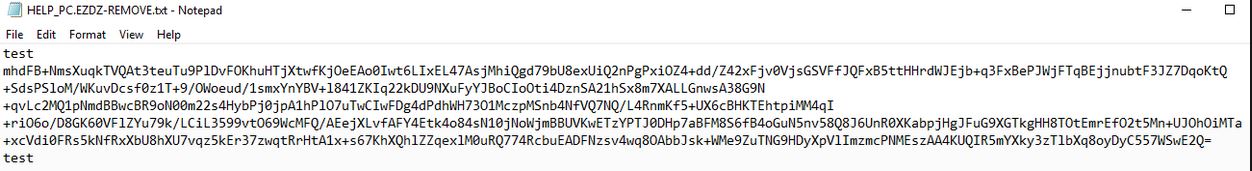
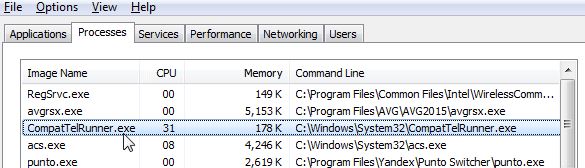
The .mogera ransomware is a new release of the STOP malware family. An unknown hacker collective is behind it, at the moment an active campaign is being spread against users worldwide. Like previous releases of this family the criminal collective…