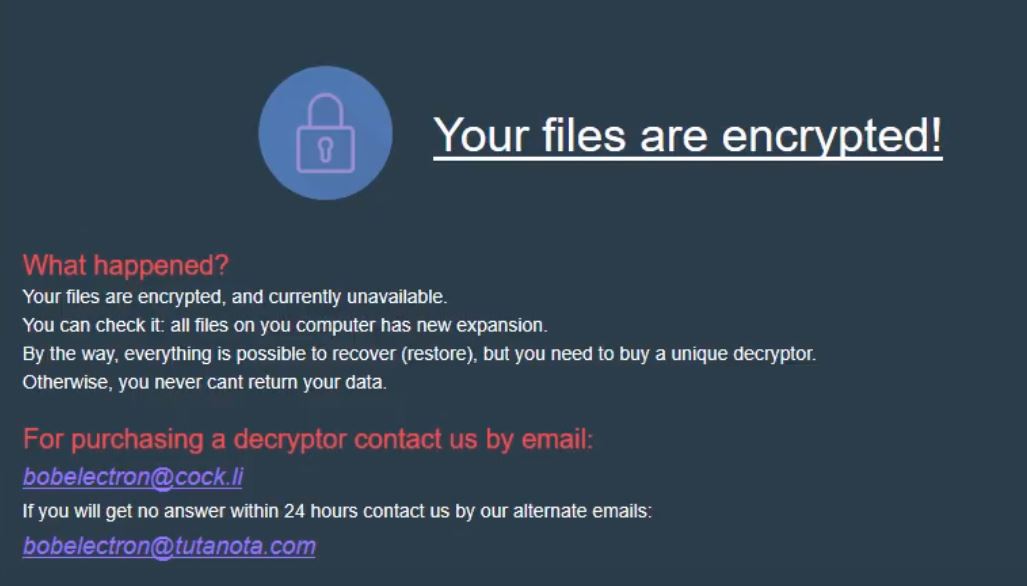
.bobelectron Virus (Globe Imposter Ransomware) — How to Remove It
.bobelectron Virus File – is it a Globe Imposter? What is Bob Electron ransomware? Bob Electron is a Globe Imposter ransomware variant. Can files encrypted by Bob Electron be recovered? Bob Electron Virus or otherwise known as .bobelectron Virus File…











![.[helpnetin@protonmail.com].com Virus File (Dharma Ransomware) – Remove It .[helpnetin@protonmail.com].com-virus-file-dharma-ransomware-note-stf](https://cdn.sensorstechforum.com/wp-content/uploads/2019/12/helpnetin@protonmail.com_.com-virus-dharma.jpg)